![图片[1]-IPSec隧道搭建-Rain's Blog](https://cdn.i-f.work/wp-content/uploads/2021/11/20211116191222924.png?imageMogr2/format/avif/)
此处省略了 MSR36-20_2的端口IP配置
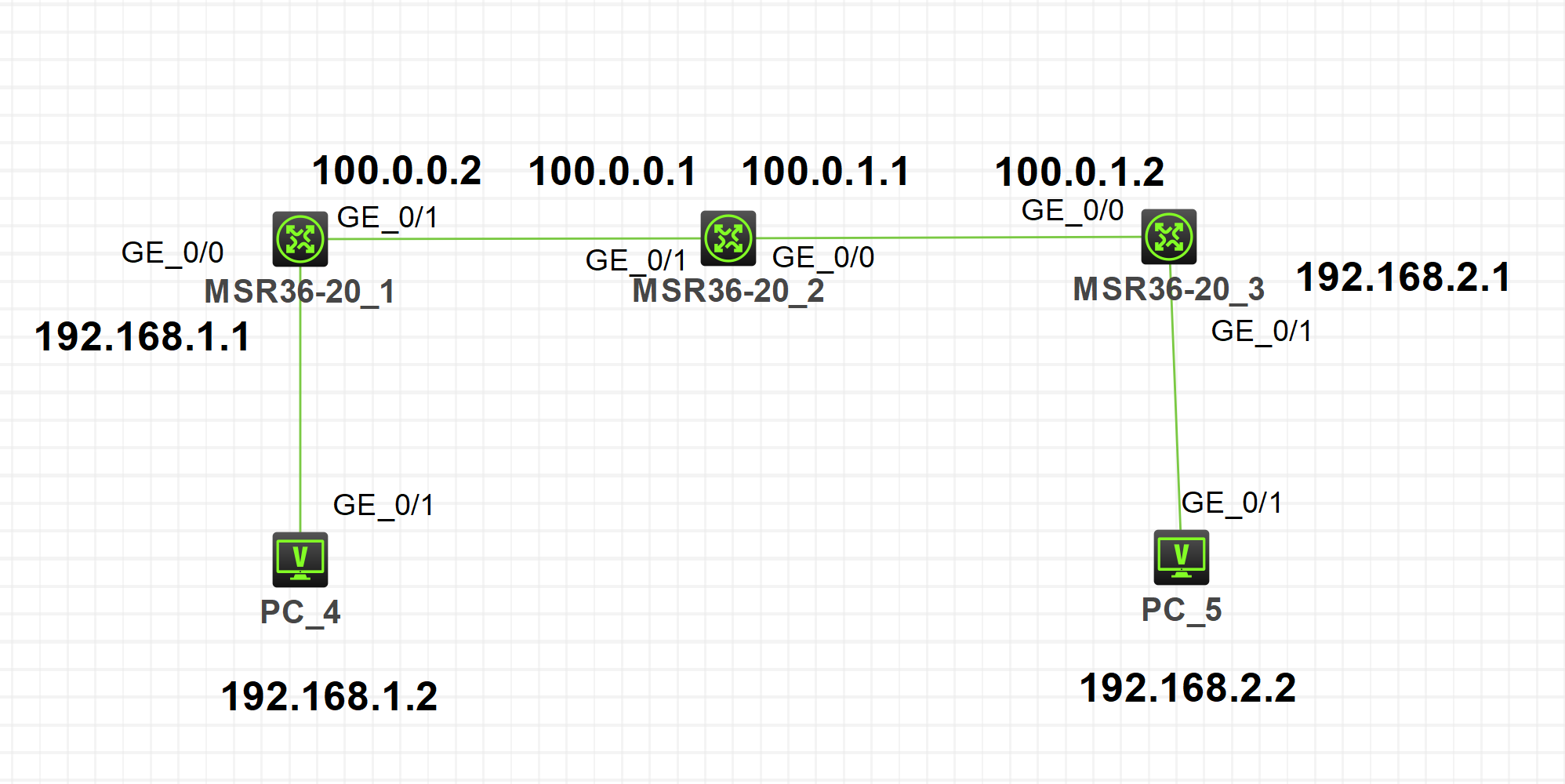
MSR36-20_1
interface GigabitEthernet 0/1
ip address 100.0.0.2 24
quit
interface GigabitEthernet 0/0
ip address 192.168.1.1 24
quit
sysname R1
ip route-static 0.0.0.0 0 100.0.0.1
#建立acl规则
acl advanced 3000
rule 0 permit ip source 192.168.1.0 0.0.0.255 destination
192.168.2.0 0.0.0.255
#建立共享密钥
ike keychain r3
pre-shared-key address 100.0.1.2 255.255.255.0 key simple 123
#建立ike模板
ike profile r3
keychain r3
local-identity address 100.0.0.2
match remote identity address 100.0.1.2 255.255.255.0
#设置ipsec保护方式
ipsec transform-set r3
esp encryption-algorithm 3des-cbc
esp authentication-algorithm md5
q
#设置ipsec触发规则、协商模式
#h3c为规则名,1为规则序号,isakmp为协商模式
ipsec policy h3c 1 isakmp
transform-set r3
security acl 3000
remote-address 100.0.1.2
ike-profile r3
qu
#设置ipesc端口绑定
interface GigabitEthernet 0/1
ipsec apply policy h3c
quMSR36-20_3
interface GigabitEthernet 0/0
ip address 100.0.1.2 24
interface GigabitEthernet 0/1
ip address 192.168.2.1 24
qu
ip route-static 0.0.0.0 0 100.0.1.1
rule 0 permit ip source 192.168.2.0 0.0.0.255 destination
192.168.1.0 0.0.0.255
ike keychain r3
pre-shared-key address 100.0.0.2 255.255.255.0 key simple 12
3
q
ike profile r3
keychain r3
local-identity address 100.0.1.2
match remote identity address 100.0.0.2 255.255.255.0
ipsec transform-set r3
esp encryption-algorithm 3des-cbc
esp authentication-algorithm md5
ipsec policy h3c 1 isakmp
transform-set r3
security acl 3000
remote-address 100.0.0.2
ike-profile r3
interface GigabitEthernet 0/0
ipsec apply policy h3c
qu查看各部分连接状态命令:
display ipsec statistics查看IPSec链路状态display ike statistics查看ike协商状态
无法联通的排错帮助:
display ipsec statistics 时,首先查看No available SA 后是否不为0,如果为0,请使用客户机互相ping一次,如果仍为零,则为ACL规则有误或未在IPSec配置内启用感兴趣流。
如果 No available SA 不为0,则进一步输入 display ike statistics 查看返回信息,如果Retransmit timeout值不为0,请检查两端的ike profile参数是否对称。
如果一端Invalid ID information不为0,而另一端为0,请检查为0端的remote-address是否正确
© 版权声明
文章版权由CC-BY-NC-SA 4.0协议分发共享
THE END
![表情[alu-34]-Rain's Blog](https://blog.im.ci/wp-content/themes/zibll/img/smilies/alu-34.png)

暂无评论内容